With the development of technology and the deep understanding of cloud concepts in various industries, the cloud has begun to spread at all levels and in various fields. It has become a kind of thinking, a trend, such as cloud computing, cloud services, cloud security and so on. They enable computing power, services, operational capabilities, and security capabilities to be centrally delivered and controlled through a single platform, making it a demanding service for thousands of businesses and individuals.
This article refers to the address: http://
How to make the cloud go deep into people's lives? The key is the provision of an open platform that enables the cloud to serve ordinary people through standard universal channels. It can be said that the lower the threshold of using cloud capabilities, the more convenient, the wider the scope of use. The ability to open cloud computing is not only convenient for end users, but also benefits third-party enterprises. They can use open interfaces and services to provide services beyond the capabilities of cloud computing itself.
1 IaaS capability open architecture
1.1 Virtualization capability is open
There are many vendors in the industry that can provide virtualization solutions such as VMWare, Microsoft, Citrix, and Xen/KVM based on open source. Various virtualization solutions have their own characteristics, but the biggest problem currently faced is that both the generated virtualization files and the virtualization management are independent and incompatible.
The current form urgently requires a standard that provides a means of virtualizing applications to all participants and reduces the problems associated with multiple, competitive, incompatible implementations. Currently, distributed management task organizations have begun to use the Open Virtual Machine (OVF) format. OVF supports multiple virtualized image formats, which can be used and loaded by virtual machines for any hypervisor. In addition, the OVF bootloader is based on digital signatures, ensuring free distribution and user benefits.
The most important participating vendors of virtualization, such as Dell, HP, IBM, Microsoft, VMware and Citrix, have joined OVF. The addition of the latter shows the importance of virtualization vendors' participation and the possibility of widespread adoption of standards. .
ZTE Corporation provides an open management platform for unified management of virtualization, which can support multiple underlying virtualization environments, as shown in Figure 1. It will also be able to support OVF in the future, and provide user-side monitoring and network management to freely create, destroy, migrate and monitor the status of each virtual machine and upper-layer applications. Since virtual machine scheduling may cause changes in network devices and load balancing devices, unified management of network devices will also be implemented. The virtualization platform provides a trusted virtualized open interface to the application layer, which allows the application system to dynamically schedule virtual machines according to their own needs. The business system is invoked through an open interface to enable a more generalized scalable business solution for automated business.

1.2 Storage capacity is open
Storage capacity is one of the most basic capabilities and the basis for all data to be processed. The current data storage mainly has three access methods: file storage, object storage, and block storage. Block storage and file storage are oriented to the underlying interface, which is generally transparent to the application; object storage belongs to the soft interface above the application layer [1].
From the perspective of the file system, cloud computing is mainly for distributed file systems, which is the core element of the cloud infrastructure. Currently, there are RedHat GFS, IBM GPFS and Sun Luster. These distributed file systems have high requirements on hardware facilities, and often require the storage nodes themselves to provide data reliability assurance. Such file systems typically provide an open interface for file access at the operating system core. The other category is similar to Google GFS products, such as open source HDFS, KFS, Alibaba's Pangu file system, etc. These products use inexpensive commercial machines to build distributed file systems and provide open interfaces in user mode.
Regardless of the internal implementation, distributed file systems need to provide reliable storage and interfaces for application access. The storage open mode implemented by the core domain is mainly to expose the bare device through the dedicated driver at the operating system kernel level, and the operating system is open to the application by using a common file system such as Ext3. The storage open mode of the user domain is a Posix interface or a proprietary private protocol interface. Using the user interface open interface has the following benefits:
The user-mode file system is loosely coupled to the operating system, which is easy to upgrade separately and has good stability.
Reduce the number of underlying interactions caused by the operating system, reduce complexity, and improve efficiency.
The interface is richer and can be better optimized.
Security is better controlled.
Of course, user mode is also open, such as the interface is intrusive to the application. If you migrate to another storage system you will need to recompile the application.
The corresponding user mode is open to the common interface mode, such as the network file system (NFS), file transfer protocol (FTP) and other standard protocols. Since these standard protocols are not formulated with distributed issues in mind, the distribution of the interfaces themselves needs to be addressed, that is, how the interfaces themselves are addressed, fault tolerant, and load balanced. At the same time, it is necessary to focus on solving the problem of read and write locks for multiple file sharing access.
ZTE's distributed file system adopts dynamic domain name system (DNS) combined with interface IP virtualization technology for common interface mode, which better solves the problem of addressing and fault tolerance, and adds an additional layer of interface layer through the server to achieve load according to capability. Equilibrium technology.
1.3 Object Storage Technology
The storage method of the direct open file system is more suitable for the construction of the private cloud. For the public cloud service for public service, we expect to be compatible with the WEB protocol (HTTP). The rapid development of the Internet poses a huge challenge to the capacity, performance and functionality of storage systems, mainly in terms of high capacity, high performance, scalability, shareability, adaptability, manageability, and high reliability and availability. There is currently no single solution on the market that meets all of these requirements. For fast-rising storage needs, Object-Based Storage (OBS) technology is a promising solution that combines high-speed, directly-accessible storage networks (SANs) with secure, well-distributed network-attached storage across platforms ( The advantages of NAS). The complexity of the underlying protocol and network structure can be well shielded by object storage. The specific characteristics of object storage are shown in Figure 2. The large-scale deployment of next-generation Internet and PB-class storage is eagerly awaiting the maturity and large-scale application of object-based storage technologies. Object storage devices (OSDs) can be built on standalone devices (such as OSD hard drives) or on distributed systems. In order to ensure the uniqueness of objects, object groups are generally divided for distributed systems to ensure that objects are unique within different object groups.
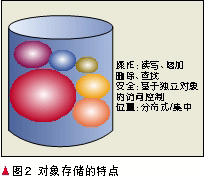
Object device internal management metadata (space management).
The object ID is a unique identifier for accessing the object (unique for each OSD device).
Figure 3 shows the OSD security model, which is a certificate-based access control system consisting of four entities: application client, security service, policy/storage manager, and object service.

Object storage generally includes the following operations: reading, writing, listing, deleting, and obtaining metadata. For example, Amazon Simple Storage Service (S3) provides object-oriented S3 for various applications.
Object storage is mainly open to applications, and various system interfaces are not yet fully unified. WebService or RESTful interfaces provide transparent access for easy application, but it is easier to provide efficient access by providing customized client access based on long links.
The distributed key-value access system developed by ZTE is a typical object storage method. It divides the data area into different buckets, and the objects in each bucket correspond to unique keys. Through the key information, the corresponding access authority verification metadata information and value information can be obtained. In order to ensure the scalability of the system, the whole system is built into a non-master network, and the automatic distribution and backup of metadata information and key value information can be achieved. To improve performance, the system supports both persistent storage and non-persistent storage mechanisms.
1.4 Block storage capacity is open
The block storage divides the storage area into small blocks of a fixed size, which is the external exposure mode of the storage space of the traditional bare storage device, as shown in FIG. 4 . The block storage of traditional devices is oriented to a single physical device, and in the cloud computing environment, block storage devices will also face a distributed environment.
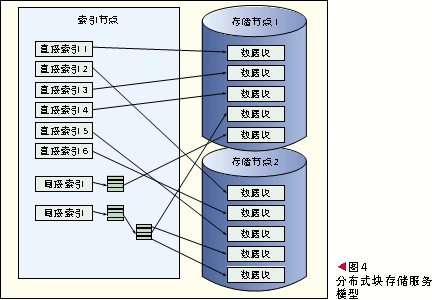
Providing block storage capability in cloud computing has an irreplaceable role in the integration of virtual machines and storage systems [2]. Because many applications are not modified or optimized in the form of cloud storage, such as most database software. Providing block storage capabilities is essential if you want to effectively deploy and use these applications in virtual machines.
One problem with block storage is poor security. Because the interface is not exposed directly to the application, but the underlying device is exposed to the operating system, there is often no better way to control the stored content.
ZTE cooperates with virtual machine technology to implement a distributed block storage access mode. With block storage, physical storage devices on multiple machines can be virtualized and re-segmented and allocated to virtual machines that need to be used. The use of block storage devices can also make good use of the old storage devices that are eliminated, and shield the different physical underlying device interfaces by storing the virtualized interface layer [3-4].
Consolidate various physical storage devices through the storage virtualization layer and slice its internal space at a fixed size. Then, the block storage interface is provided to the client, and the plurality of sliced ​​small block storage areas are uniformly scheduled by the storage virtualization layer to form a volume size required by the client, as shown in FIG. 5. Each small slice is directly mapped by the interface to the client's block access request as a physical machine's block access request.

1.5 IaaS capability open security considerations
For commercial system users, efficient access, reliability, and ease of use of the system are one aspect, but the ultimate decision on whether to use cloud computing as the enterprise's basic service is open-ended security.
(1) Management of privileged users
Privileged users, such as administrators of operators, must be strictly regulated because of their absolute power.
(2) Compliance with regulations
Although cloud computing companies provide services through operators, laws and regulations require companies that provide services to comply with and assume, not the operators themselves. Therefore, the objective requirement is not only that the service company must meet the relevant regulatory requirements, but also the operators that provide services to them must meet the relevant requirements to avoid legal risks.
(3) Control of the geographic location of the data
Privacy protection varies from country to country. As a borderless network service, it must be able to meet the privacy rules of users in specific geographic locations to ensure compliance with the regulations of the place of service. Some countries and regions have limited physical storage addresses for sensitive data, and service providers must be able to meet these requirements.
(4) Data isolation
Cloud services are geared towards many users, so data must be effectively isolated and, if necessary, capable of providing physical isolation of data.
(5) Data recovery capability in case of failure
When a failure occurs, how to quickly restore services and data, and effectively back up data, must be considered.
(6) Support ability for investigation
Some laws, such as the Sarbanes-Oxley Act, require traceability of all data operations. In the face of an audit or legal investigation, the service provider must be able to effectively provide relevant operational data.
(7) Permanent availability
Suppliers of cloud services may not be able to provide services permanently, for example, HP recently stopped the web album service. Migrating data and services from one carrier to another or to their own data center is a very important security factor when the service is terminated.
2 PaaS Capability Open Architecture
2.1 Virtualization-based business cloud hosting and deployment
This application scenario is mainly the operation of the Internet Data Center (IDC) [5], typically Amazon's Elastic Compute Cloud (EC2), which can support a variety of different operating systems and development environments. This type of platform generally provides users with the following features:
flexibility
The system generally allows the user to relatively freely customize the type, quantity, resource usage, and even geographic location of the running instance, and can be adjusted at any time according to user requirements.
low cost
With the service provided by the operator, small businesses do not have to purchase expensive equipment and network equipment themselves, and can charge according to the capacity and time of the service.
safety
Operators typically provide a full range of security measures, such as Secure Shell Protocol (SSH)-based access authentication, firewall settings, etc., while allowing users to monitor their applications themselves.
Ease of use
In addition to providing basic virtual machine services, operators also provide other basic services such as object storage, databases, and message pipes. Applications can be used directly without having to build these infrastructures.
Fault tolerance
The system generally provides a certain network and storage fault tolerance mechanism. Once a failure occurs, the data can be guaranteed to be reliable and the user service is as stable as possible.
There are three main types of access interfaces provided:
Virtual machine remote access interface. Mainly through the unified verification of SSH services and reliable data protocol (RDP) service provision.
Manage service interfaces. Provide users to monitor the status of the virtual service cluster and create, delete, and adjust virtual nodes.
Business service access interface. It is provided entirely by the customer's services running inside the virtual machine, but the system can provide a unified security access service.
2.2 Business capability is open
The business open platform provides a modular interface for network or business execution. Developers can quickly integrate different modules to create new web applications by calling various functions provided by the Open Application Programming Interface (API) [6]. There are many such services, the most famous of which is Google's map service. Telecom companies can also open some telecommunications-related services, such as mobile phone location query services, SMS mass-sending services, etc. Taobao also opened APIs related to many user goods and transactions according to its own needs.
To quickly integrate these different services with materials, many companies also offer Mashup rapid development tools such as Yahoo's Pipe, Google's Mashup Editor, and Microsoft's Popfly.
In the business capability open platform, a developer sandbox [7] is generally required to assist developers in simulating real system operations during the development phase without interfering with the operation of the real system. Figure 6 is a typical deployment structure of the business capability open platform.

The service capability open platform must have access control function for client access. On the one hand, the client side's authentication and authentication, only the legally authenticated client can use the service service; on the other hand, the access rights and calls of different levels of customers The frequency needs to be verified in case the wrong client or malicious program causes a service exception or data anomaly.
2.3 Online Service Hosting Mode
The online business hosting platform is an enterprise resource planning (ERP), customer relationship management (CRM) or general service provider through an open platform, allowing third parties to develop their own services and provide services externally on the hosting platform. These third-party developed services have their own distinct user and independent requirements, but need to use the basic resources provided by the platform to provide external services. Typical such as Google's App Engine, Saleforce's force.com and eBay and Taobao's hosting platform. The resources, users, and data of the third-party service sharing platform focus on developing demand solutions that effectively complement the capabilities that the platform does not have. For example, 45% of eBay's current products are available through third-party apps.
Each platform includes a standard service framework, data access interfaces, and specific programming language support. After being deployed on the platform, the platform can automatically allocate computing resources according to the heat of access and so on, and smoothly expand.
2.4 Version management and dynamic upgrade of open service interfaces
External services inevitably involve the version management and upgrade strategy of the interface. To ensure the continuity of the service, we must ensure that the version can be upgraded without interrupting the service, ensuring compatibility and availability between different versions of the client. . Figure 7 illustrates how forward-compatible service interface design and upgrade processes are performed.

2.5 Secure service opening
The key to ensuring stable and reliable service is to provide trusted services. It has three meanings: it needs to have the means to verify the identity of the user of the service, only authorized users can access specific services; the service itself is reliable, illegal users or illegal access It will affect normal user access; the data storage of the service is safe and reliable, and only trusted people can access the trusted data.
There are some practices to ensure access security:
Access the authorization and signature of the app. Before the client system or application accesses the cloud service, it must be authenticated by the cloud service provider. The certification result is delivered to the client in the form of an authorization code. For each subsequent visit, the client will need to present an authorization code or request an authorization code to sign. The results returned by the system are also signed by the system certificate to achieve mutual trust between the two parties [8].
Timestamp mode. For asynchronous systems, the timestamp and the unique client ID are used as the serial number of the request, and the system returns the same way to construct the serial number for adaptation.
Idempotent check. The client can generate a unique serial number, and the server can detect whether the client command is repeatedly sent. If there is a duplicate, it will directly discard it. Idempotent checks ensure that all service requests are one-time and unique, and will not execute even if they are maliciously intercepted and replayed through a network device.
Controlled by a secure whitelist. Through the whitelist system, the system guarantees that only clients that have been authenticated by security can access it, usually through an authentication certificate, which is the most restrictive access restriction.
If an application developed by a third party is involved, the reverse call mode of the system can be used to ensure that the authentication information input by the user is not obtained by the third-party application, and the third-party application user can be notified whether the relevant authorization is available.
Figure 8 illustrates the relationship between the user federation mode. The specific steps for implementing unified user opening in the federated user mode are as follows:

(1) Users access third-party applications.
(2) The third-party application directs the user to the platform side for authentication.
(3) The platform authenticates the user to the interface of the platform.
(4) The platform generates a token, and invokes a third-party application interface in reverse to deliver the user, the user token, and the authorization information to the third-party application.
(5) A third-party application binds the user to the user token.
(6) When a third-party application needs to access user data on the platform side, the user token is presented, and the user authority can be accessed.
(7) After the access is completed, the third-party application notifies the platform to cancel the token.
3 SaaS Capability Open Architecture
Force.com's CRM software giant Salesforce has built an enterprise-class cloud computing platform that allows its customers to develop applications for internal use on Force.com. In 2009, Force.com launched a new distribution channel: Value Added Retail (VAR). These VARs are typically consultants and system integrators for IT consulting for large companies that can develop applications based on Force.com and package these applications along with Force.com's underlying database for sale to large companies. For example, a HR consultant can develop a recruitment application based on Force.com data and sell it to the Fortune 500.
These VAR partners not only distribute Force.com's cloud computing platform, but also distribute additional features such as mobility, storage, site building, and sandbox development. There are many possibilities to develop enterprise applications for the Force.com platform. Currently, there are more than 120,000 applications developed around Force.com, such as supply chain management, cargo tracking, brand management, accounts receivable, complaint handling, and more.
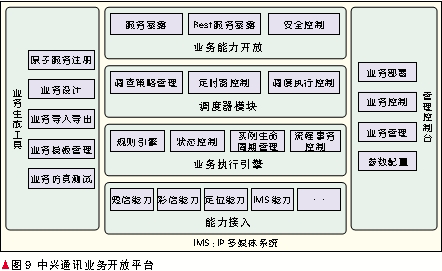
For telecom services, ZTE has created an open platform for telecommunications service capabilities. Third parties can customize the capabilities of telecommunications services through this platform. This platform is also capable of combining various atomic services of the telecommunication service and combining them into a complex service for external programming.
ZTE's telecom capability open platform is mainly composed of business development environment, business execution environment and management module, as shown in Figure 9.
4 Conclusion
As a general service infrastructure, cloud computing must be able to be used by various businesses and applications to reflect value, otherwise it is only a closed dedicated system. Just like water and electricity, there must be standardized water pipes and circuits to be able to introduce thousands of households. Therefore, all levels of cloud computing need to be open and follow relevant open standards to achieve universal cloud services. In the IaaS layer, there are OVF virtualization standards, standard file access, and object storage and block storage. The PaaS layer is a service provisioning and capability open platform. The service itself is ever-changing, but we can follow some common design principles to ensure the service interface. The smooth upgrade and the security of the service; the SaaS level is a complete service offering. At this level, ZTE pays attention to how to provide a platform, so that third parties can also quickly develop various services.
5 References
[1] Liu Peng. Cloud computing [M]. Beijing: Publishing House of Electronics Industry, 2010.
[2] Huang Ran. The virtualization format is open to drive the virtualization process [EB/OL]. (2010-01-12).http://virtual.51cto.com/art/200901/106039.htm
[3] FACTOR M, METH K, NAOR D, et al. Object Storage: The Future Building Block for Storage Systems [C]// Local to Global Data Interoperability-Challenges and Technologies: Proceedings of the 2nd International IEEE Symposium on Mass Storage Systems and Technologies (MMST '05), Jun 20-24, 2005, Sardinia, Italy. Washington, DC, USA : IEEE Computer Society, 2005: 119-123.
[4] SNIA-Storage Networking Industry Association.OSD: Object Based Storage Devices Technical Work Group [EB/OL].http:// _ activities/workgroups/osd/.
[5] Yang Zhiqiang, Zhang Yan. Building a mobile Internet application infrastructure - creating an "open garden" [J]. ZTE Technology, 2009, 15 (4): 1-4.
[6] Wang Yinghao. Network storage technology [J]. SME Management and Technology, 2009 (4): 238.
[7] Li Wei. Based on the SAML Federal Identity Management Mechanism [C]//The 19th National Conference on Computer Technology and Applications (CACIS2008), July 15-20, 2008, Leshan.
[8] KING. Salesforce pushes the Force cloud computing architecture [N] for open source. Computer World, 2008-01-19.
Wewow has series 3 axis gimbal, such as
1. A1 legend with powerful function. Can fit with smartphone, action camera+mirrorless camera.
2. A5 gimbal: a simple easy to use 3 axis gimbal, with app function
3. P3, Wewow old type 3 axis gimbal, without app function.
4. Alite: the lastest gimbal with selfie stick 3 axis gimbal.
Three Axis Gimbal
Three Axis Gimbal,Fashion Style Three Axis Gimbal,Three Axis Handheld Gimbal,3 Axis Camera Gimbal
GUANGZHOU WEWOW ELECTRONIC CO., LTD. , https://www.stabilizers.pl